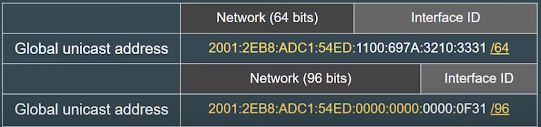
Questions and Answers to some TTPs involving Malicious Processes
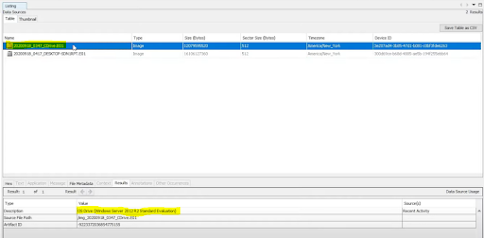
When examining ongoing processes for any signs of a breach, is it possible that a malicious process can go under the same name of a legitimate process? As someone who runs multiple windows of chrome, I expect to see more than one chrome.exe amongst my processes. Malware may run another process under the same name. Additionally I often see malware run processes under a misspelled name at least in some CTFs, is this seen in other breaches?