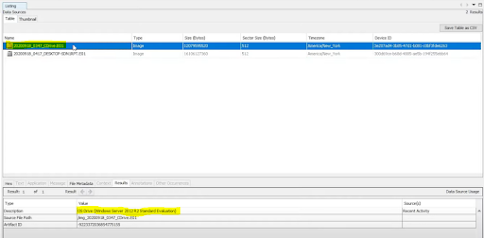
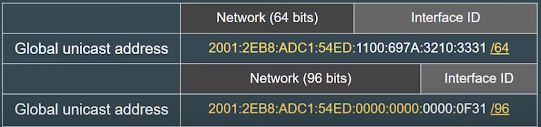
Linux Host & Network Information Gathering
For this portion of my notes I will be focusing on collecting information useful for someone attempting to leverage a breached system to further their attack. Here I would be talking about some of the tools and resources that is native within a Linux system that may help scope out a scene. Additionally mentioning some tactics the attacker may use when sniffing or scanning an area with minimal detection.