Memory Analysis Practice
Lessons and experience taken from this challenge
- Understanding the advantages and goals of memory analysis
- Exposure to some memory forensics tools
- Examine the network connections of processes
- Recognize malicious processes
- Extract plaintext malware samples from memory
- Develop a list of IOCs to scope an investigations
- IP Addresses that may be flagged by other security institutes.
- Processes that don’t normally connect to the internet.
- Processes that don't normally exist natively to the windows operating system.
- Unusual amount of network traffic.
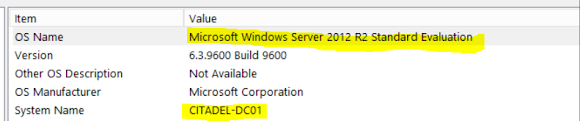
Suspicious Processes within DC Server
Offset(P):0x20fc7590Protocol:TCPv4Local Address:10.42.85.10:62613Foreign Address:203.78.103.109:443State: ESTABLISHEDPid:3644Owner: coreupdater.exCreated: Nothing
Malfind
Malfind is a tool used by examiners that does good work in narrowing in on process IDs that are suspicious. This tool examines for any signs of injected code/DLLs in user-mode memory, based on characteristics such as VAD tags and page permissions. VAD, Virtual Address Descriptors, provides useful information about the address space of a specified process. They provide details about the PTE Protection Bits, inheritance of the page and wherever the page is being shared between processes.
With that said, we are provided some processes that we may examine more closely. Here I keep an eye out for any red flags within the assembly code. Primarily for assembly statements that follow a A-B-A pattern. This is a sign of code that was injected in this process. Malfind directs our attention to “spoolsv.exe”, which in fact holds this pattern as well as a XOR statement. This statement is known to cipher input.
Carving Processes with Malfind
Malfind has the ability to carve out processes from memory. This will allow me to examine the files with other AV tools. ClamAV reports 4 infected processes involving two types of malware, Meterpreter and Razy. After some searching, one can understand that Meterpreter is a payload typically assembled under Metasploit. It attempts to reside within memory through DLL injection. This malware will communicate with the network providing an interactive shell. These operations occur within native processes, it avoids to create new ones. Razy happens to be ransomware.
Fortunately, this tool lists out the memory address of where the detections took place. If we cross reference this with our previous findings, all four results lay within “spoolsv.exe”.
Further Analysis of Infected Processes
Here I copied these infected processes into its own directory and examine them through FLOSS. FLOSS is a tool that attempts to deobfuscate strings within Windows Portable Executable files. Successful deobfuscation may reveal other IOCs such as malicious domains and file paths.
We do find the same IP address associated with coreupdater.ex. Further validating the thesis that this process involves communicating with the attacker.
Some details to take note involve the parental relationship between the processes that we confirmed malicious. While spoolsv.exe relationship with services.exe doesn’t raise any red flags at the moment, process 2244 for coreupdater is gone. Additionally this process seems to have no active threads at this time.
Here we will use "pstree -v" to allow us to see the file path to these two processes, of which lead back to the system32 directory.
Filepath that lead to spoolsv and coreupdater
These file paths could help for when an examiner investigates any other red flags within the disk. This should be listed as a IOC from incident response purposes. Additionally it must be said that any change done in this directory requires admin privileges. Implying that our attacker has someone gotten themselves this type of access.
Conclusion
At this point, one has enough IOC to serve as pivot points when examining PCAP files or the Desktop Disk Image. I will end this post from here as it covers the examination made on this artifact. Before that however, here is a recap of everything that was covered.
- Confirmed the type of operating system of the server.
- Performed a netscan of processes.
- Reviewed these processes that reveal one of which is unfamiliar by windows.
- Examined the associated IP address of which resolves somewhere in Thailand.
- Used Malfind to reveal that spoolsv.exe has characteristics common to injected code.
- Used Malfind to carve and dump all processes of which are scanned by a AV program.
- AV program informs us of malware within these processes, so FLOSS is performed to deobfuscate them.
- The same IP address is found, further validating a connection between these two processes.
- Used pstree to find out that system32 was likely accessed and the filepaths involve are now known to us as IOCs.
Comments
Post a Comment