When examining ongoing processes for any signs of a breach, is it possible that a malicious process can go under the same name of a legitimate process? As someone who runs multiple windows of chrome, I expect to see more than one chrome.exe amongst my processes. Malware may run another process under the same name. Additionally I often see malware run processes under a misspelled name at least in some CTFs, is this seen in other breaches?
So despite being able to run multiple instances of the same process into RAM, one has to keep in mind that the original executable file exists singularly within the disk. So here are some options to get a malicious process going.
- Infect an existing process with one’s malware
- Create a process with a misspelled name such as flrefox.exe, maybe in the same file path as firefox.exe
- Create a process of a correct name but within a different file path, so that one does not overwrite and disrupt normal operations.
|
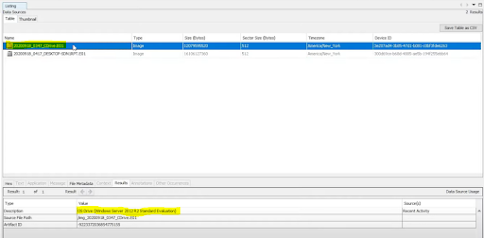
What if an incident responder did not take a screenshot of the server, before he had shut it down for collection? What are other methods to prove the type of operating system of a computer?
| One method of confirming the operating system for a data artifact is to simply check some the disk image itself. A tool such as autopsy would check from some of the windows registries to inform the user of this.
|
What are Content Distribution Nodes and why is it relevant to seeking any red flags involving IP addresses?
A content delivery network (CDN) refers to geographically distributed servers that provide speedy delivery of internet content. Example of such internet content includes HTML pages, javascript files, stylesheets, images, and videos; which are cached for convenience. A CDN can also keep a site secured with fresh TLS/SSL certificates allowing a high standard of authentication, encryption, and integrity. CDNs may also yield some sort of reputation seen by security institutes based upon the amount of malicious IP addresses observed that connect to this node. Example map of CDNs, and how they distribute web traffic
|
What is the traffic light protocol?
Traffic Light Protocol (TLP) refers the labeling of threat intelligence and how sensitive/restrictive it is to share. The state of the TLP goes as white, green, amber, and red. From the least restrictive to the most.
Red- No sharing other than a predefined list
Amber- shared among members of a community
Green- sharing amongst a community
White- sharing is allowed to anyone |
The malfind command helps find hidden or injected code/DLLs in user mode memory, based on characteristics such as VAD tag and page permissions. However, what is a VAD tag?
| Virtual Address Descriptors provides details of a specified process. Information involving PTE Protection Bits, inheritance of the page and how the page is shared between processes. |
Additionally what is the significance to "MZ" in the Hex section?
| Files will have a header that the operating system must read so they may determine how to interpret the file. For most windows executables will denote this as "MZ". Which is lovely to find for examiners when they suspect a file has been involved in something malicious. Essentially allowing malware to be able to run and execute its function. |

Comments
Post a Comment