Lab Examples and the Cyber Kill Chain
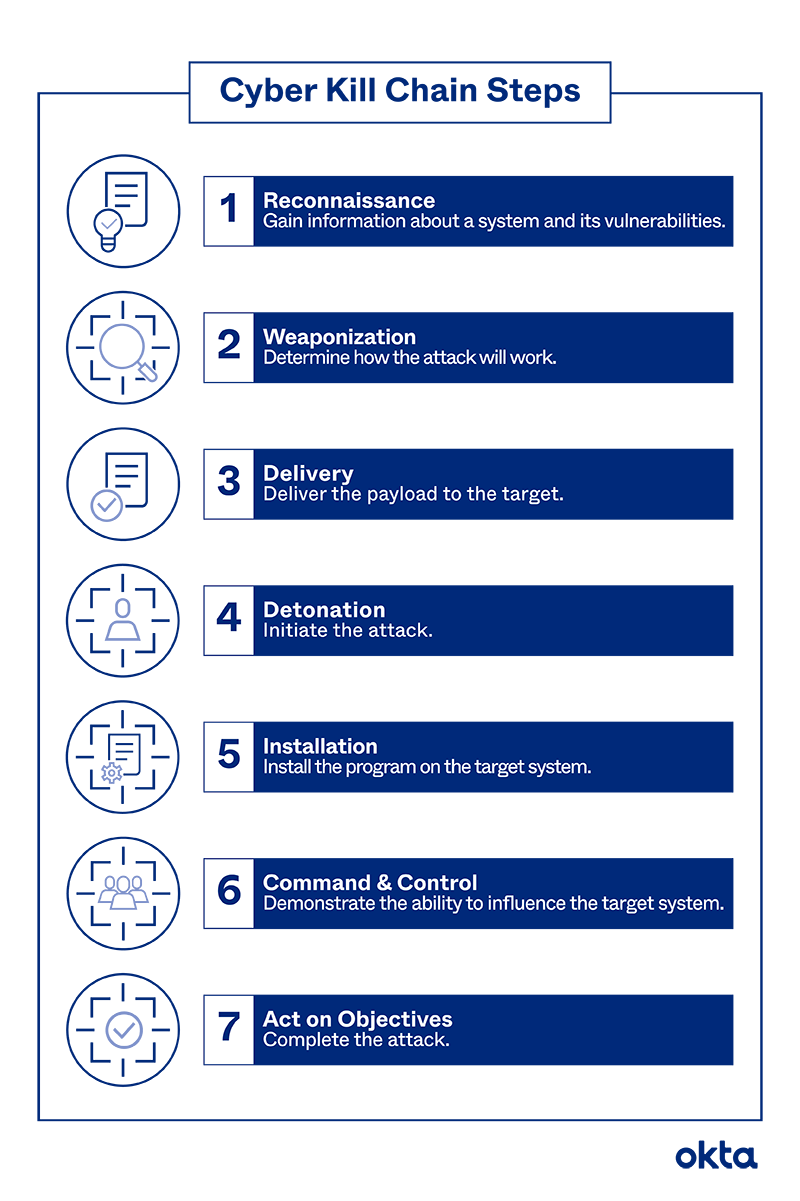
Cybersecurity Kill Chain
A model that describes stages of an attack (developed by Lockheed Martin). This model assists the red and blue team view how attacks may be deployed.
Reconnaissance: research, identify, targeted systems such as probing external network nodes for open ports.
Passive Recon: Where an attacker is able to observe the victim without any direct interaction
Examples
Whois: a tool that looks up the domain registration information. Could be used to phish admins from their contact info for or attempt to target the authoritative DNS servers.
Nslookup: DNS lookup tool that reveals information to the target IP address. Such as a type of site such as a mail server.
Data access search engines: sites that attempt to collect information on devices that connect to the internet such as Shodan and Censys.
Social media: media that provide content on an entity's presence online
Search engines: internet searches that provide general details of a target such as google or bing
Active Recon: Where an attack observes the victim with some sort of interaction
Types
Fingerprinting: directly gets details of a targeted system such as using nmap to examine observable ports.
Vulnerability scanning: monitors an organization’s security vulnerabilities in their network.
Web application scanning: Scan for website vulnerabilities and characteristics.
Weaponization: Attackers will engineer their malware to leverage one’s vulnerabilities, additionally with the intention being covert.
Delivery: the attacker will adopt a medium to drop malware into one’s IT environment. Popular examples would be emails, websites, and removable media.
Exploitation: The parameters of the victim’s security measure have been breached. Allowing for the attack to deploy their own scripts, install tools, and modify security certificates.
Installation: The act of installing malware or any other assets that may further the effectiveness of the attack.
Command & Control (C2): Allows the attackers to perform operations within the network, such as having a reverse shell.
Actions on Objections: Complete objective of the breach for instance this could be simple surveillance, encrypted data for ransom, or leak data.
Lab 1
Objective:
In this lab, you will exploit a remote system, analyze web logs, and perform incident response on a compromised host. (infoseclearning.com cybrary)
Outcomes:
Scan a network with nmap/zenmap
Exploit a system using Bruter
Use remote desktop using the stolen credentials from Bruter
Overview:
For this lab we will act as the attacker attempting to breach a network and afterwards respond to this breach. As the attacker, one would use tools such as nmap/zenmap to sniff any open ports that are external to this network. Utilizing a brute force tool to attempt to develop any valid credentials to breach this network. Once this goal is completed, one will follow through the incident response workflow. Where one would seek out log files to find any indicators of compromise. Overall detailing that the breach occurred through weak passwords and open ports.
Attack procedure
Use nmap or zenmap to scan the network, find a ftp open port, use bruter to find a password, establish a RDP session with credentials.
IR procedure
Logged in to the compromise computer, mount IR tools, output details about network interfaces, user login times, network activity, and processes running. Develop the hash of this report. Afterwards, look into system 32 to find login logs.
Typical commands used to collect IOCs
Lab 2: File Baselines
Objective: develop a baseline that one can verify the integrity of one’s files within a linux and windows environment.
Comments
Post a Comment